Protect yourself from Git identity theft#

Git supports signing commits with a private key and GitHub (& many other git servers) supports verifying those commits with a public key.
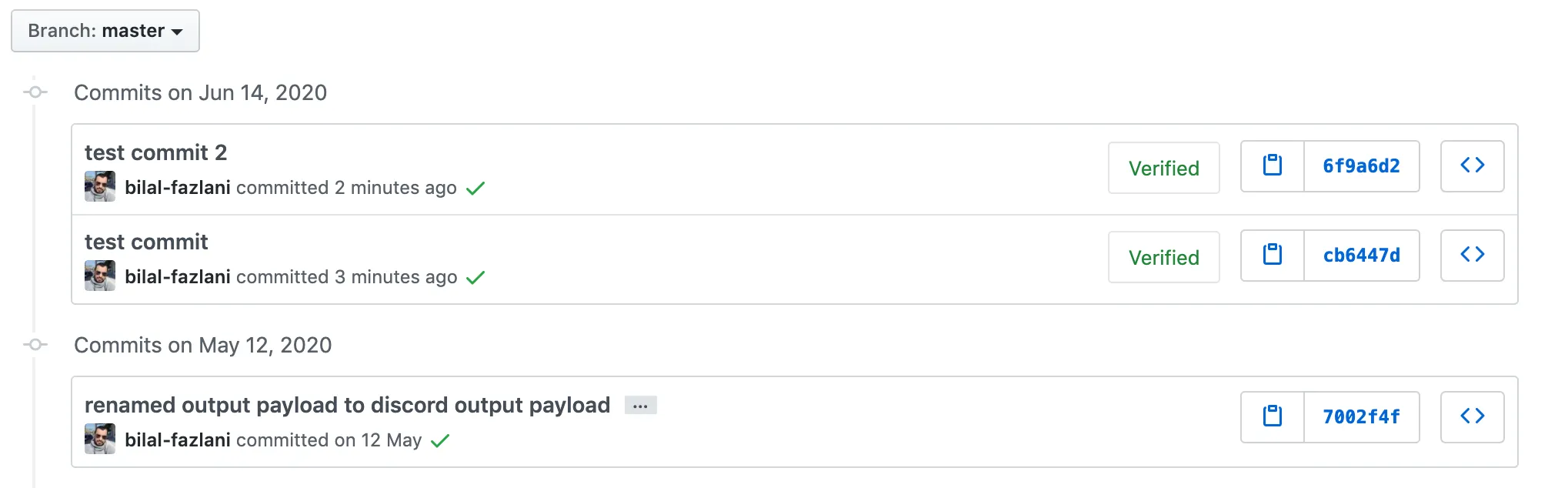
Signed and verified commits are marked as “Verified” by GitHub. This provides a level of verification for the commit.
Why sign the commits?#
When creating a new commit, I can simply do this to set user-name and email which does not belong to me.
git config user.name "some-other-user"
git config user.email "other-user@gmail.com"
There, done. Now GitHub shows my commit as other user’s commit. 😱 I will leave it to you to imagine what evil things can happen now.
Important
Signed commits are a way to prove authenticity of a commit
For a successful verification, Github requires that you first verify your email address using a verification email. A verified email can be used to sign new commits and should match the email id of the commit. If they don’t match or if the email used to sign commit is not verified for the GitHub account, then the commit is shown as Unverified.
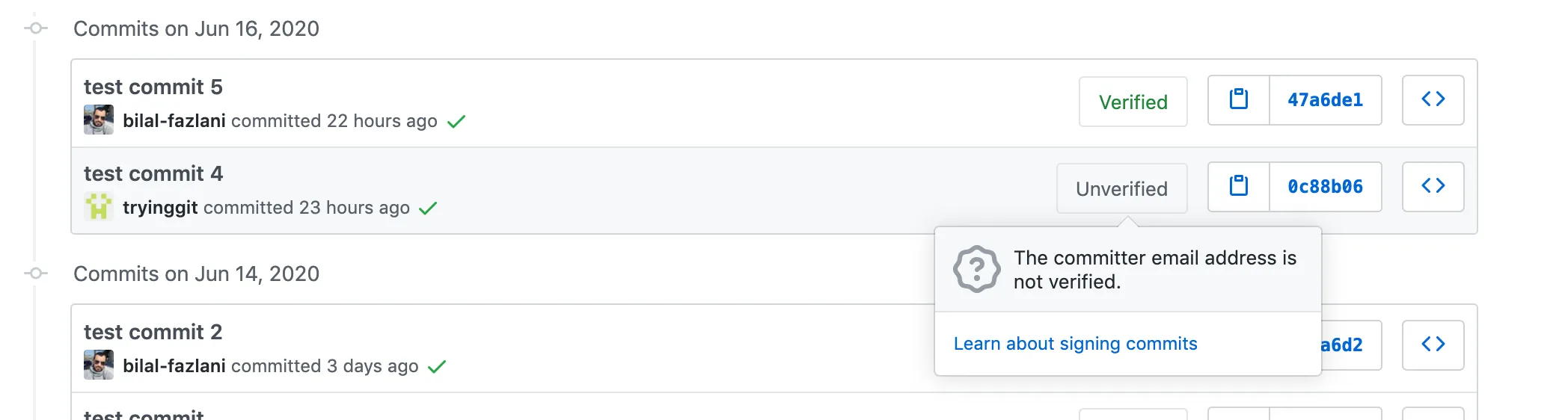
Remember to protect your private key though 😅
Let’s get started#
Generating a new GPG key-pair#
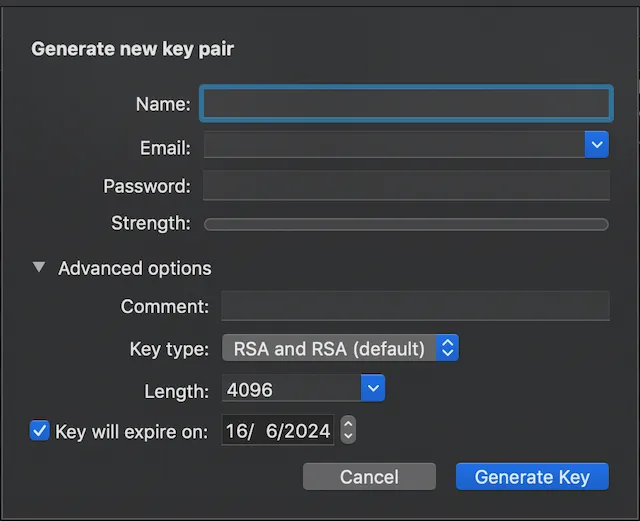
We need to create a pair of private and public keys. Private key will be used for signing git commits and the public key will be used by GitHub to verify our commits. You can use GPG Suite if you are using a Mac.
Or you can create the key pair using the following command:
gpg --full-generate-key
You will need to ensure you have installed gnupg on your machine to get gpg command

Configuring git to sign commits#
First, we need to configure the key id for git. Key Id can be seen with the following command:
gpg --list-secret-keys --keyid-format LONG
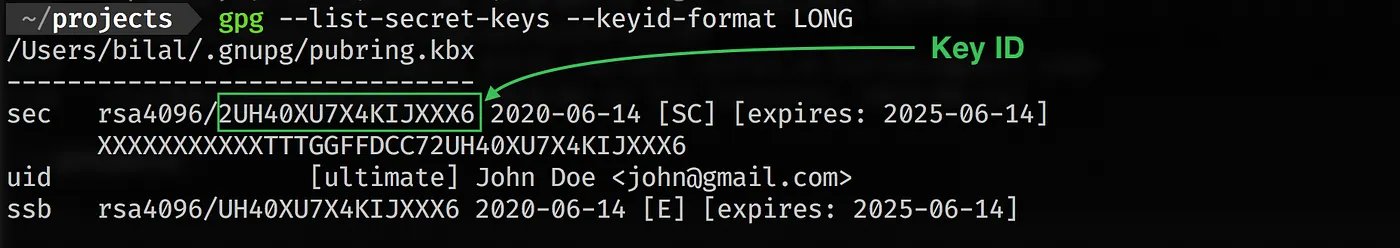
Key Id is can also be viewed in the GPG Keychain (GPG Suite)
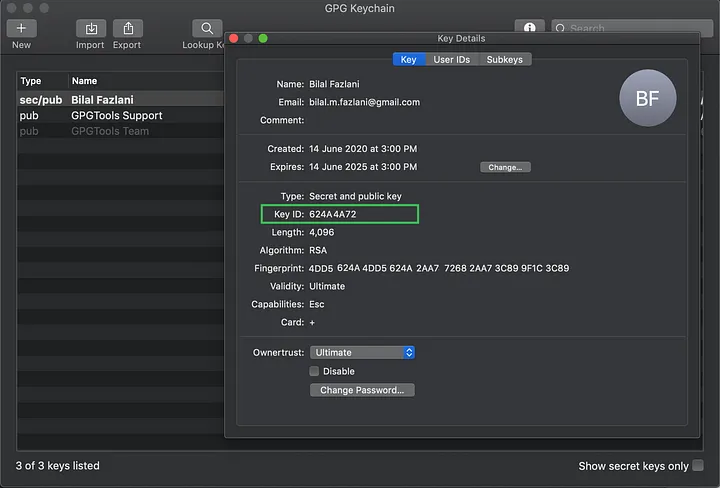
The following command will configure key id for all repos (global setting)
git config --global user.signingkey <KEY ID>
If you omit the --global flag, it will set the key only for the current repository.
Now we can start signing commits. A commit can be signed every time you commit with -S flag. For example:
git commit -S -m "commit message"
Or else, you can configure git to always signs all commits by automatically for you.
git config --global commit.gpgsign true
Configuring Github to verify commits#
We need to upload the public key to Github so it can use to verify the commit signature. If you are using GPG Suite, then you can simply copy the public key as shown below
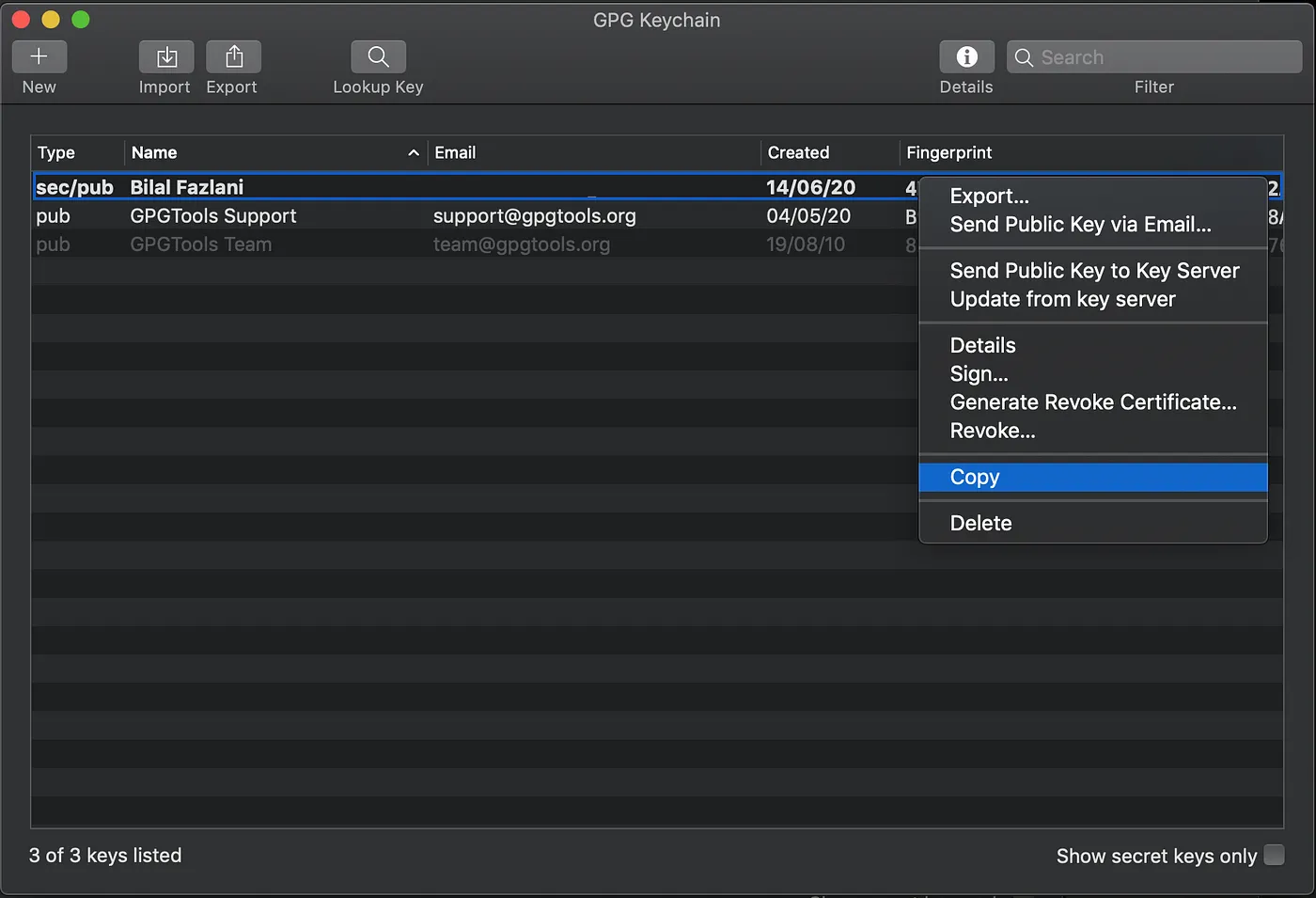
This can also be done using the command line. You can use the following command to print the public key
gpg --armor --export john@gmail.com
Or to directly copy it to clipboard, use “pbcopy”
gpg --armor --export john@gmail.com | pbcopy
A public key starts with text -----BEGIN PGP PUBLIC KEY BLOCK----- and ends with -----END PGP PUBLIC KEY BLOCK----- with a lot of text in between.
Now that we the public key, we can upload it to GitHub. Visit the URL: https://github.com/settings/gpg/new and add the copied public key here
Once the key is registered with Github, we are ready to make new signed commits and push them! 🎉
Tip 1
GPG Suite is very helpful if you are on a Mac. I would suggest using it because it helps save and use password for private key using Keychain. With this, you don’t have to type the password of the private key every time you want to sign a commit.
Tip 2
You can use the same public key to upload to another git server such as BitBucket too.